Modernizing Workplaces With Microsoft Security Products
Protect your infrastructure, data, and workforce. Be fearless by using an all-encompassing, best-in-class, and AI-driven security strategy. With Microsoft security solutions, you can achieve the entire aspects of business security.
Secure everything: With integrated corporate security solutions created to function across platforms and cloud environments, you can protect your entire organization.
Streamline the complicated: Utilize unified management solutions designed to leverage the human expertise present inside your organization to prioritize the appropriate risks.
Get what others overlook: Advanced automation, AI, and expertise enable you to swiftly identify risks, take swift action, and strengthen your security posture.
Grow and modernize your future: You are free to expand, create, and reinvent your business because a complete security solution gives you peace of mind.
Let’s explore the leading Microsoft security solutions.
Microsoft Defender
To provide comprehensive defense against complex assaults, Microsoft 365 Defender is a centralized pre- and post-breach enterprise defense package that primarily combines surveillance, mitigation, inspection, and response across endpoints, identities, emails, and applications.
Security experts can establish the complete breadth and impact of the threat, including how it entered the environment, what it affected, and how it now affects the enterprise, using the integrated Microsoft 365 Defender solution. Then, Microsoft 365 Defender automatically intervenes to stop the attack and self-heals the compromised user IDs, mailboxes, and endpoints.
Microsoft Defender is divided into two categories which includes Microsoft 365 Defender and Microsoft Defender for Cloud.
The Microsoft Defender product family falls into the following categories,
- Microsoft Defender for Endpoint
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
In addition to these, Microsoft 365 Defender closely integrates with Azure Active Directory Identity Protection, App Governance, and Microsoft Data Loss Prevention to offer comprehensive defense against complex cyberattacks.
Microsoft Entra
The new product family, Microsoft Entra, includes all of Microsoft’s identity and access capabilities. In addition, Microsoft Azure Active Directory (Azure AD) and two new product categories, decentralized identity and cloud infrastructure entitlement management (CIEM), are all part of the Entra family. The Entra family of products, which offer identity and access management, cloud infrastructure entitlement management, and identity verification, will contribute to ensuring that everyone has secure access to everything.
The Microsoft Entra product family falls into the following categories,
- Azure Active Directory
- Microsoft Entra Permissions Management
- Microsoft Entra Verified ID
- Microsoft Entra Workload Identities
- Microsoft Entra Identity Governance
- Azure Active Directory
For the sixth successive year in 2022, Microsoft is acknowledged as a Leader in the Gartner® Magic Quadrant™ for Access Management
According to Microsoft,
“Microsoft Azure AD, our hero identity and access management product, will be part of the Microsoft Entra family, and all its capabilities that our customers know and love, such as Conditional Access and passwordless authentication, remain unchanged. Azure AD External Identities continues to be our identity solution for customers and partners under the Microsoft Entra family.”
Microsoft Priva
Consumers and businesses are increasingly concerned about privacy and worries about how personal data is handled are growing. People worldwide are affected by rules and legislation like the General Data Protection Regulation (GDPR) of the European Union and the California Consumer Privacy Act (CCPA), which give individuals the right to manage the data that an organization has obtained.
Organizations must adopt a “privacy by default” approach to satisfy legal regulations and increase customer trust. Therefore, organizations require a comprehensive solution to handle typical problems like:
- Preventing privacy concerns brought on by human error in the growing volumes of unstructured data
- Assisting staff in adopting ethical data handling methods and educating them to identify and address problems
- Recognizing the hazards associated with the quantity and type of personal information they store and share
- Efficient and prompt response to petitions for the rights of data subjects
- Preventing privacy concerns brought on by human error in the growing volumes of unstructured data
It enables you to overcome these difficulties to accomplish your privacy objectives.
The Microsoft Priva product family falls into the following categories,
- Microsoft Priva Privacy Risk Management
- Microsoft Priva Subject Rights Requests
- Microsoft Priva Privacy Risk Management
Priva assesses the information held by your company in the preceding Microsoft 365 services under your Microsoft 365 tenant:
- SharePoint Online and Exchange Online
- Enterprise OneDrive
- Microsoft Teams
- SharePoint Online and Exchange Online
Microsoft Purview
Microsoft Purview, formerly known as Azure Purview, is a collection of tools created to offer a solution for centralized data governance across the whole environment of a business, including on-premises databases, cloud databases, SaaS data, and practically any other data source or platform.
In other words, Microsoft Purview is a full-featured collection of data management tools that may assist you in governing, safeguarding, and managing your whole data estate. Microsoft Purview helps you comprehend and govern the data across your estate, secure that data wherever it lives, and strengthen your risk and compliance posture in a much easier way than conventional solutions. It combines the former Azure Purview and the former Microsoft 365 Compliance portfolio in one brand and, over time, in a more unified platform.
In September 2021, Azure Purview was made generally available. After then, Microsoft declared that Azure Purview would change to Microsoft Purview in April 2022. What’s the distinction? Microsoft Purview is a fusion of the Microsoft 365 Compliance portfolio with the previous Azure Purview.
The Microsoft Purview product family falls into the following major categories,
- Risk and compliance solutions
- Unified data governance solutions
- Risk and compliance solutions
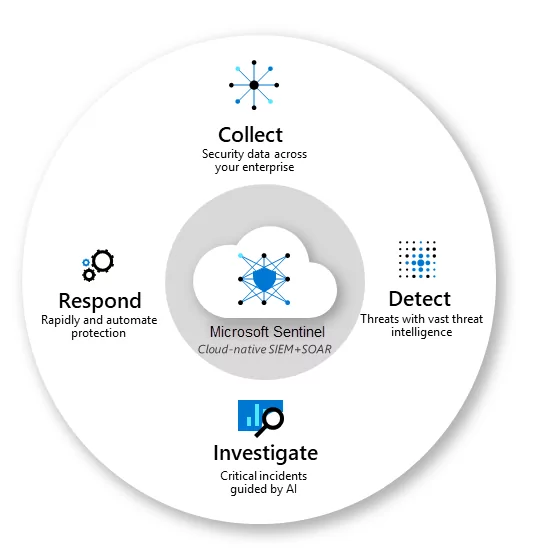
Microsoft Sentinel
With SIEM innovated for the modern world, threats can be seen and stopped before they cause harm. Microsoft Sentinel provides your bird’s-eye perspective of the entire company. Utilize the cloud and extensive intelligence acquired from years of Microsoft security expertise. Use artificial intelligence to detect threats more quickly and intelligently (AI). Eliminate the setup and management of security infrastructure and elastically scale to match your security needs—all while spending up to 48% less than traditional SIEMs.
For security event analysis in on-premises and cloud environments, use Microsoft Sentinel. Typical use cases comprise:
- The visualization of log data
- Finding hazards and alerting
- Analysis of security-related occurrences
- Active threat detection
- Automatic responses to security cases
- The visualization of log data
Microsoft Sentinel centralizes your threat-gathering, detecting, responding, and investigating efforts. Threat exposure, alert detection, threat response, and proactive hunting are made possible by the threat intelligence and intelligent security analytic capabilities it offers.
It operates following a cycle that begins with log management and includes automated alert replies before moving on to schema normalization, data validation, detection, and inquiry.